Cybersecurity Studies and Notes
Tryhackme
Junior Security Analyst Intro
- A career as a Junior Associate Security Analyst
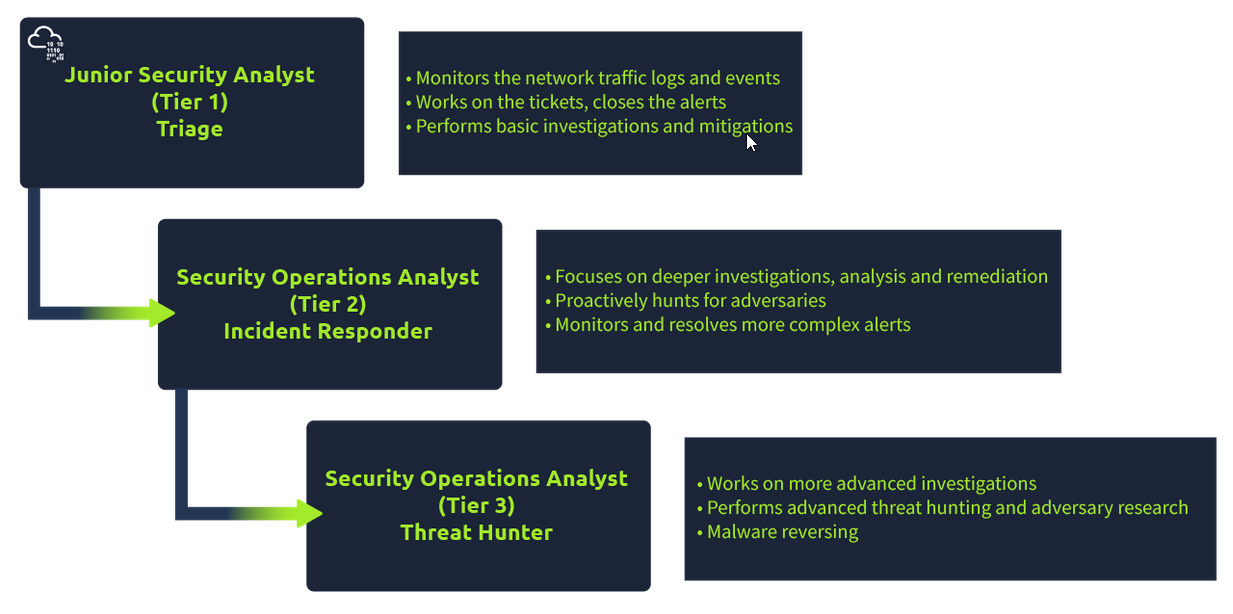
- SOC (Security Operations Center)
- A day in the life of a Junior Associate Security Analyst
Pyramid of Pain
- A concept being applied into Cybersecurity to improve the effectiveness of CTI (Cyber Threat Intelligence)
- Hash Values - Uniquely identify a data. Result of hashing algorithm
1.1 MD5 - message Digest
1.2 SHA1 -
1.3 SHA2 -
1.4 SHA 256 - IP Address
2.1 Fast Flux - Fast Flux is a DNS technique used by botnets to hide phishing, web proxying, malware delivery, and malware communication activities behind compromised hosts acting as proxies. The purpose of using the Fast Flux network is to make the communication between malware and its command and control server (C&C) challenging to be discovered by security professionals. - DNS
3.1 Punycode - Way of converting words that cannot be written in ASCII, into a unicode ASCII encoding.
3.2 URL shortener - A URL Shortener is a tool that creates a short and unique URL that will redirect to the specific website specified during the initial step of setting up the URL Shortener link
- Host Artifacts - Host artifacts are the traces or observables that attackers leave on the system, such as registry values, suspicious process execution, attack patterns or IOCs (Indicators of Compromise), files dropped by malicious applications, or anything exclusive to the current threat.
- Network Artifacts - A network artifact can be a user-agent string, C2 information, or URI patterns followed by the HTTP POST requests.An attacker might use a User-Agent string that hasn’t been observed in your environment before or seems out of the ordinary. The User-Agent is defined by RFC2616 as the request-header field that contains the information about the user agent originating the request.
- Tools
- TTP - TTPs stands for Tactics, Techniques & Procedures. This includes the whole MITRE ATT&CK Matrix, which means all the steps taken by an adversary to achieve his goal, starting from phishing attempts to persistence and data exfiltration
Cyberkill Chain
Established by Lockheed Martin on 2011. Defines the steps used by a malicious actor.
Kill Chain means Structure of an attack (military concept)
Cyber kill chain - lifecycle
Attack Phases - how attacks are manifested
- Reconnaissance - Real
- Weaponization - Warriors
- Delivery - Deliver
- Exploitation - Every
- Installation - Intense
- Command & Control - Command
- Actions on Objectives Accurately
Incident Handling Process Review
- Preparation
- Detection and Analysis
- Containment, Eradication and Recovery
- Post incident Recovery
incident handling has two main activities, which are investigating and recovering. The investigation aims to:
- Discover the initial 'patient zero' victim and create an (ongoing if still active) incident timeline
- Determine what tools and malware the adversary used
- Document the compromised systems and what the adversary has done
Preparation
Protective Measures - DMARC is an email protection against phishing built on top of the already existing SPF and DKIM. The idea behind DMARC is to reject emails that 'pretend' to originate from your organization.
Detection and Analysis
Initial Investigation
- Date/Time when the incident was reported. Additionally, who detected the incident and/or who reported it?
- How was the incident detected?
- What was the incident? Phishing? System unavailability? etc.
- Assemble a list of impacted systems (if relevant)
- Document who has accessed the impacted systems and what actions have been taken. Make a note of whether this is an ongoing incident or the suspicious activity has been stopped
- Physical location, operating systems, IP addresses and hostnames, system owner, system's purpose, current state of the system
- (If malware is involved) List of IP addresses, time and date of detection, type of malware, systems impacted, export of malicious files with forensic information on them (such as hashes, copies of the files, etc.)
Incident Severity & Extent Questions
When handling a security incident, we should also try to answer the following questions to get an idea of the incident's severity and extent:
- What is the exploitation impact?
- What are the exploitation requirements?
- Can any business-critical systems be affected by the incident?
- Are there any suggested remediation steps?
- How many systems have been impacted?
- Is the exploit being used in the wild?
- Does the exploit have any worm-like capabilities?
The last two can possibly indicate the level of sophistication of an adversary.